The recent ransomware attacks on Colonial Pipeline and JBS led to a flurry of calls to ban Bitcoin (and cryptocurrency generally) as enabling and incentivizing these attacks.[1] Given the difficulty of tracking the perpetrators, the argument goes, cryptocurrency is a uniquely appealing method of payment to hackers. Take away the hackers’ easy ability to get paid and you reduce the incentive to carry out the attack. Bitcoin defenders point out that lots of things are used in criminal activity that we aren’t prepared to ban. Cryptocurrency critics reply that, for all its promise, cryptocurrency remains devoid of a single positive use case, and that its primary uses are for speculative investment and criminal activity.[2] On Sunday, June 6, former President Trump remarked that Bitcoin was “a scam” that competed with the U.S. dollar.[3] Then on Monday, June 7, federal authorities announced that they had traced and seized millions of dollars that Colonial Pipeline paid in the attack, the first such publicized ransomware payment recovery.[4] What, if any, implications does that recovery have for the debate over banning cryptocurrency?
This explainer unpacks the recent events, their meaning, and suggests what might be coming next in terms of law enforcement and regulatory activity for cryptocurrency.
What Happens in a Ransomware Attack?
A hacker penetrates a company’s computer system and encrypts the company’s data, thereby bringing operations to a halt. The hacker then holds the data hostage until a ransom is paid. If the demand is made for payment in Bitcoin or another cryptocurrency, the victim has to open an account on a cryptocurrency exchange, buy Bitcoin, and send it to the hacker’s virtual wallet in exchange for the decryption key. The key allows the company to restore access to its data so its operations can resume. The hacker, meanwhile, moves the payment through cryptocurrency exchanges and “mixers”—services that blend cryptocurrency from various sources to hide its origin, thereby laundering the ransom payment.[5]
Why is Cryptocurrency the Payment of Choice for Ransomware Hackers?
Cryptocurrency is useful for ransomware payments due to its pseudonymous quality; even if you see the final destination wallet into which the ransom payment is deposited, you can’t see who owns or controls the wallet. This has allowed ransomware attacks to be carried out with relative impunity. This impunity, in turn, has led to an explosion of ransomware attacks and the prevalence of a ransomware company DarkSide, which leases its ransomware to hackers in exchange for a portion of any ransom paid. DarkSide, the recipient of the Colonial Pipeline ransom payment, has collected more than $90 million in ransom payments in the last year, according to Elliptic, a blockchain analytics firm.[6]
Ransomware attacks demanding cryptocurrency have gotten worse in both nature and number. In past years, ransomware hackers stole data and threatened to release it or sell it online.[7] A terrible act to be sure, but not one that necessarily paralyzes a company. More recently, however, hackers have increasingly brought operations to a halt by encrypting files necessary for continuing the business. Attacks are, therefore, more likely to be debilitating, giving the hackers more leverage.
Hackers have used this leverage to strike harder and more frequently. The number of ransomware cases reported to the FBI went up by approximately 66% in 2020,[8] and the average ransomware payment has quadrupled in less than two years, going from $12,000 in Q4 2019 to $54,000 in Q1 2021.[9] A report by blockchain analytics firm Chainalysis noted that although prior to Q1 2020, it never saw a ransomware payment above $6 million, since then it has identified at least one per quarter. [10]
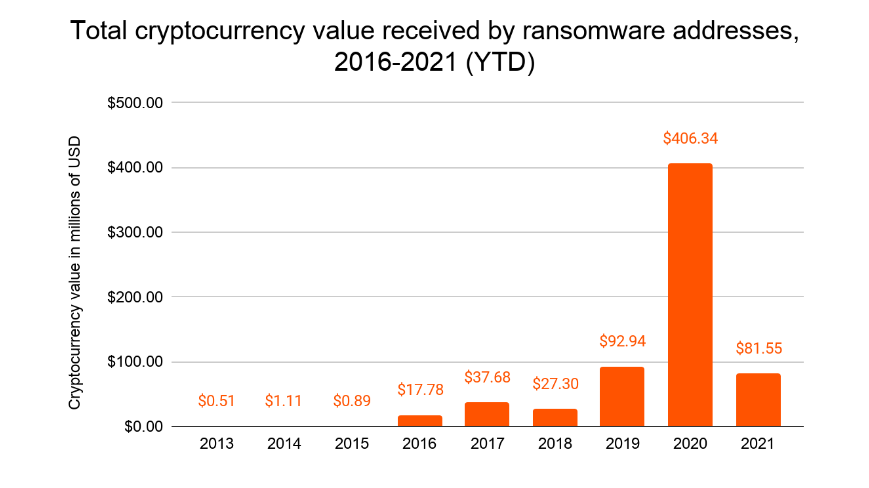
Source: Chainalysis: Ransomware 2021: Critical Mid-Year Update [Report Preview].
In terms of total value paid, Chainalysis found that cryptocurrency value received by ransomware addresses went from just over $37 million in 2019, to just over $92 million in 2019, to more than $406 million in 2020. And as of May 10, 2021, more than $81 million in cryptocurrency had been sent to ransomware addresses.
So Why Not Ban Cryptocurrency?
Notwithstanding the concerns about cryptocurrency facilitating ransomware attacks, a ban is generally thought by those in the industry and the federal government alike to be overbroad, logistically impractical, and likely to cause competitive harm to the U.S.[11] Although assorted calls for a ban have been published recently,[12] federal regulators and law enforcement officials are optimistic that the regulation will catch up to the risk.
For instance, Chairman of the SEC Gary Gensler, who previously taught a course at MIT on cryptocurrency and blockchain, has described himself as an “optimist” on the blockchain technology used to record Bitcoin transactions, saying that he wants it to succeed while protecting financial stability, investors, and consumers.[13] In April, SEC Commissioner Hester Peirce commented that “it would be a foolish thing for the government to try to do that [ban Bitcoin],” that a “government could say it’s not allowed here but people would still be able to do it and it would be very hard to stop people from doing it [transacting in Bitcoin],” adding that “we would be missing out on the innovation around bitcoin and other digital assets if we decided to try to stop them.”[14] The same month, Michael Morell, former Deputy Director of the CIA authored a paper arguing (among other things) that the blockchain ledger on which Bitcoin transactions are recorded is a very effective and under-utilized crime-fighting and intelligence gathering tool.[15]
Morello cites current and former federal officials of the view that it “is easier for law enforcement to trace illicit activity using Bitcoin than it is to trace cross-border illegal activity using traditional banking transactions, and far easier than cash transactions,” and who compare the blockchain ledger recording Bitcoin transactions to “having the whole world be a witness to paying someone $2,000 in a dark alley.”[16] To be fair, having the whole world witness the payment is not the same as having it witness the identity of the payee. In any event, Morello’s confidence in law enforcement’s tracing ability was born out on June 7 when federal authorities announced the recovery of millions of dollars paid in the Colonial Pipeline ransomware attack.[17]
How Did the FBI Recover the Ransom Payment?
In this case, the FBI seemed to catch a lucky break, as no tracking through mixers or other obscuring channels was required. Within days of the May 8 ransom payment by Colonial Pipeline, the analytics firm Elliptic identified the Bitcoin wallet that received the payment and observed that it had received Bitcoin payments since March totaling $17.5 million.[18] Although most of the payments were moved out on May 9, just over two million dollars remained in the same account it was paid into until it was seized by the FBI through a court-approved seizure warrant.
At the same time, the actions of identifying the wallet and obtaining a seizure warrant, by themselves, would not give the FBI access to the ransom payments. The FBI also needed the private key to access the wallet. The agent affidavit submitted in support of the seizure warrant application states that the FBI was in possession of the private key, but does not specify how it was obtained. Nor has the FBI said publicly how it obtained the key. A few possibilities noted in the press are that (1) the FBI was tipped off by someone associated with the attack, or associated with DarkSide, (2) one of the hackers was careless in discussing the key over a communications channel and the FBI had already obtained a search warrant for (as the FBI had been investigating DarkSide for the last year, or (3) from “leveraging information it got from Bitcoin or from the cryptocurrency exchange where the money had been bouncing from one account to another since it was first paid.”[19] Given that some of the money never left the original account into which it was deposited, presumably this means that law enforcement gained insight from the other payments that were moving between accounts. For now, however, we are left to speculate as to how the key was obtained.
What Does the Recovery Mean for Banning or Regulating Bitcoin?
Given that law enforcement has an ability to track and recover ransomware payments in a way that even a week ago seemed unlikely, the recent recovery could both deter such attacks and quiet the calls to “ban cryptocurrency” generally. But recovering the payment is not the same as identifying and prosecuting the hacker. Nor is it the same as preventing such attacks in the first place.
De-anonymizing transactions would help achieve both the prevention and prosecution aims, as regulators seem to agree. A would-be hacker whose identity is discoverable is more likely deterred from attempting such an attack. In terms of new standards, the Financial Action Task Force (“FATF”), a group of 200 countries and jurisdictions that sets AML and other standards for virtual assets and virtual asset service providers (“VASPs”), released a draft of new guidance in March that seems to suggest prohibiting peer-to-peer cryptocurrency exchanges and privacy coins (i.e., Anonymity-Enhanced Cryptocurrencies (“AECs”) that use additional features to conceal information about transactions).[20] Concern about privacy coins is not limited to FATF. Michael Morell commented that the most popular privacy coin—Monero—sees a higher percentage of illicit activity within its overall transaction volume, that one known ransomware group (Sodinokibi) accepts payments only in Monero and that some ransomware operators offer discounted rates to victims who paid in Monero or other AECs.[21] South Korea banned Monero and other privacy coins late last year, and many cryptocurrency exchanges choose not to list Monero given the risks associated with it.[22]
We can also expect greater enforcement of existing Know Your Customer (KYC) and AML obligations and standards. For instance, cryptocurrency exchanges, custodial wallet companies, and crypto payment processors (among others) must register as money services businesses with FinCEN, have AML programs that specify the KYC information collected, and appoint a compliance officer to monitor transactions and file Suspicious Activity Reports (“SARs”) and Currency Transactions Reports (“CTRs”) for transactions in excess of $10,000. These processes are important not only for potential law enforcement tracking in the event a crime occurs, but obviously for crime prevention and for building consumer trust and confidence, a necessity for widespread adoption of cryptocurrency. New applicants need to know that criminals are being screened for and kept out.
Greater federal resources are also being committed to enhance law enforcement sophistication in tracking and prosecuting crypto crimes. [23] As mentioned in a prior client advisory, the U.S. Department of Justice (“DOJ”) released its Cryptocurrency Enforcement Framework in October 2020, and the IRS (among other agencies) has been contracting with blockchain analytics firms to work on tracing the “untraceable” privacy coins and other currencies, a project that seems to have been at least partially successful.[24] Just a week ago, DOJ launched the Ransomware and Digital Extortion Task Force dedicated to combating combatting ransomware attacks, which FBI Director Christopher Wray has compared to the national security threat the country faced after terrorist attacks of the September 11, 2001.[25] The new task force, a public-private partnership, includes representatives from the FBI and the United States Secret Service as well as major tech and security companies,[26] and is expected to recommend tougher KYC regulations and licensing requirements as well as centralize efforts to combat and respond to ransomware attacks.
[1] See, e.g., Lee Reiners,
Ban Cryptocurrency to Fight Ransomware, WSJ (May 25, 2021),
https://www.wsj.com/articles/ban-cryptocurrency-to-fight-ransomware-11621962831?page=1; Jacob Silverman,
Want to Stop Ransomware Attacks? Ban Bitcoin and Other Cryptocurrencies, The New Republic (June 2, 2021),
https://newrepublic.com/article/162589/ban-bitcoin-cryptocurrencies-stop-hacker-ransomware.
[2] The authors are not endorsing this view, to be clear, and will discuss use cases in a future explainer.
[5] See, Jeff Stone,
Ransomware hackers launder bitcoin through just a handful of locations, researchers find, Cyberscoop (Jan. 26, 2021). The alleged mastermind of one Bitcoin mixing service, Bitcoin Fog, was arrested in April on money laundering and other charges. Press Release, U.S. Dep’t of Just., Individual Arrested and Charged with Operating Notorious Darknet Cryptocurrency ‘Mixer’ (Apr. 28, 2021),
https://www.justice.gov/opa/pr/individual-arrested-and-charged-operating-notorious-darknet-cryptocurrency-mixer.
[7] See, e.g., Jaclyn Diaz,
D.C. Police Department Victim of Apparent Ransomware Attack, NPR (Apr. 27, 2021),
https://www.npr.org/2021/04/27/991116344/d-c-police-department-victim-of-apparent-ransomware-attack;
Cognizant hit by ‘Maze’ ransomware attack, Reuters (Apr. 18, 2020),
https://www.reuters.com/article/us-cognizant-tech-cyber/cognizant-hit-by-maze-ransomware-attack-idUSKBN2200YA; Lee Matthews,
Ransomware Hackers Have Started Leaking City of Pensacola Data, Forbes (Dec. 31, 2019),
https://www.forbes.com/sites/leemathews/2020/12/31/ransomware-hackers-have-started-leaking-city-of-pensacola-data/?sh=42b25224994b.
[12] See, e.g., Lee Reiners,
Ban Cryptocurrency to Fight Ransomware, WSJ (May 25, 2021),
https://www.wsj.com/articles/ban-cryptocurrency-to-fight-ransomware-11621962831?page=1; Jacob Silverman,
Want to Stop Ransomware Attacks? Ban Bitcoin and Other Cryptocurrencies, The New Republic (June 2, 2021),
https://newrepublic.com/article/162589/ban-bitcoin-cryptocurrencies-stop-hacker-ransomware.
[13] Cyptocurrencies: Oversight of New Assets in the Digital Age: Hearing Before the H. Comm. On Agric., 115th Cong. 30 (2018) (statement of Hon. Gary Gensler).
[23] Although we also expect increased enforcement activity in the area of federal securities and tax law, these are less connected to ransomware and beyond the scope of this explainer.
[24] See, Kelley Phillips Erb,
IRS Will Pay Up To $625,000 If You Can Crack Monero, Other Privacy Coins, Forbes (Sept. 14, 2020),
https://news.bitcoin.com/chainalysis-and-integra-win-1-25-million-irs-contract-to-break-monero/. In early 2019, DHS contacted with CipherTrace to work on tracing Monero transactions, as its popularity in darknet transactions was increasing. The next year, CipherTrace filed two patents in connection with that activity. See CipherTrace Files Two Monero Cryptocurrency Tracing Patents, CipherTrace (Nov. 20, 2020),
https://ciphertrace.com/ciphertrace-files-two-monero-cryptocurrency-tracing-patents/
[View source.]